13 June 2025
Sophisticated new phishing attacks
Most people are aware of the risk of clicking malicious links. However, iBizify would like to highlight a relatively new, growing security threat. The attack is sophisticated, executed by coordinated human teams, assisted by AI. It can bypass standard security mechanisms, and is performed discreetly.
It targets users of Microsoft 365 Business services, and other similar services. This phishing attack is particularly concerning, given that it uses sophisticated methods to effectively bypass multi-factor authentication – which is a common first line of defence against phishing attacks and password compromises.
⚠️ These emails will usually come from someone you know. The email address will be true and correct. It may pass standard security checks.
The cause
The breach begins with a phishing email or message that comes from a familiar address, such as a colleague, friend, or family. They may include the sender’s legitimate email signature, their name, and other details, making them look extremely convincing.
Here are a couple of examples of such email content, but the email may take any form:
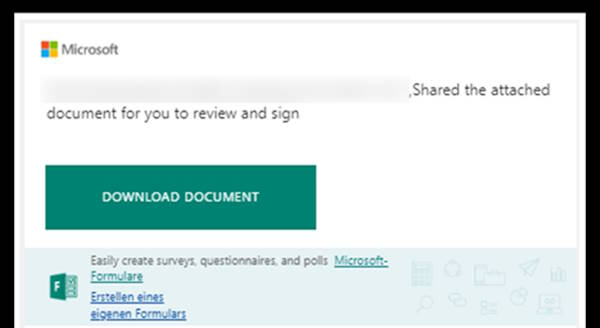
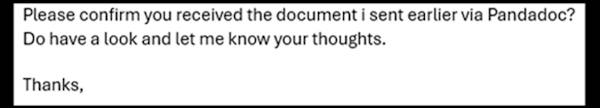
These attacks often evade the detection of standard security software, due to the verified sender, and the use of an “innocent” service, such as OneNote, Pandadoc, amongst others.
The effect
The following describes the general nature of attacks iBizify has evaluated. In fact, every attack and its process can be very different.
Exercise extreme caution if you receive an email asking you to open a document or click a link, even if you know the sender. These links may lead to phishing sites that collect your login details and register a new multifactor authentication device for further access. Attackers could gain full remote access to your mailbox and other services.
Unlike regular attacks in the past, these are often handled in by human teams, who are on standby to maximise the attack in real time.
Typically, the attacker downloads copies of all accessible information. Within the mailbox, mail rules are configured to conceal activities, followed by the dispatch of hundreds or thousands of phishing emails to contacts. Sent items are automatically deleted, and incoming emails are also removed to hide concerned replies. An automatic response is sent to further convince recipients of the legitimacy of the phishing email.
After a breach, attackers often analyse stolen data to understand the victim’s systems and maximise their gains, delaying the actual attack by days or weeks. This delay increases the impact, as victims may be unaware of the breach for some time, making the original cause harder to identify.
When your email account is compromised in this way, attackers typically collect addresses from all your past emails, not just your contacts in the address book. The impact is thus far greater than similar attacks in the past.
If an email link or request for action is unexpected, don't click or respond - even if you know the sender. If you're unsure why you received the document, verify by phoning the sender first.
⚠️ Never use email to question the validity of an email you have received. If the sender’s account has been compromised, the response may well come from the attack team!

What to do about it
If you believe you may have clicked through and shared your details, please contact iBizify or your trusted IT service / support provider for urgent advice. I urge you to remain vigilant and take precautions to protect your accounts and information.
To help prevent such breaches, and be better prepared should you experience one:
- Always exercise caution and maintain vigilance. Consider implementing continuous awareness training such as KnowBe4 to ensure that you and your colleagues remain alert and aware of potential threats.
- Use strong unique passwords, and multifactor authentication. Use a business-grade password management solution such as Keeper Security to securely store passwords and other sensitive information.
- Review if it is possible to prevent phishing attacks altogether by deploying a phish-proof, password-free solution such as AuthN by IDEE.
- Use a secure, encrypted backup and security service such as Sentinel that stores data separately from your main systems. Include both cloud-based data and critical devices.
- Use managed IT services. The IT landscape is constantly evolving, so ensure your service is properly set up, administered and maintained by a reliable and knowledgeable service provider. Manage365 provides such a service for Microsoft 365 users.
- Deploy a managed security solution such as iBizify's Secure365 for Microsoft 365 users: Installing anti-virus and a few software packages is insufficient. A suitable combination of tools, front line and fallback security layers, along with managed monitoring, alerts, and reporting, introduces a critical human element to this ongoing challenge.
- Auditing: Make sure you have a full record of who and what is being accessed and why.
- Conditional access: define who, how, why and when anyone can access your system – whether they have a password or not.
- Always keep your online service configurations, computers, devices and security baselines up to date to minimise vulnerabilities.
- Do not allow your staff to use insecure, unpatched or outdated devices to connect to your IT services. iBizify's Sentinel offers endpoint security, backup, identifies and patches vulnerabilities.
Need help? iBizify has supported many business and personal clients, including IT companies and service providers, in handling and preventing attacks and breaches. We have assisted with email, website, phone, and other online service attacks.